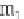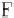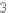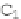Cryptography Reference
In-Depth Information
4.3.1.4 Output Feedback Mode
Output feedback mode (OFB) is similar to CFB in that it uses a block cipher to
generate a pseudo-random stream that is Xor-ed with the message. The starting point
for this stream is a random IV of length
n
(the block length of the cipher) and the
subsequent streammembers are obtained by successively applying the forward cipher
function so that, in contrast to CFB, the key stream is generated independently from
the ciphertext blocks. In OFB mode the IV need not be unpredictable and hence it
need not be random but it must be a
nonce
(in the cryptographic sense), i.e., it must be
unique to each execution of the encryption operation with the same key (we discuss
this aspect below). However, choosing it at random is a good way to ensure that the
IV is, with high probability, not repeated across encryptions with the same key. The
encryption algorithm can be described as follows:
Algorithm 4.7. OFB encryption
.
Input
:An
l
-block message
m
=
m
1
...
m
l
, and a block cipher key
k
.
Output
: The ciphertext
Enc
(
k
,
m
)
=
c
1
...
c
l
.
Initialization
:
IV
←{
0
,
1
}
n
, chosen at random.
Key Stream Computation
:
r
0
:=
IV
;
for
i
from
1
to
l
do
r
i
:=
F
k
(
r
i
−
1
)
end do
;
Encryption
:
for
i
from
1
to
l
do
c
i
:=
m
i
⊕
r
i
end do
;
return
c
1
...
c
l
.
The decryption algorithm is practically the same, except that now the roles of
plaintext and ciphertext are interchanged and the IV is given as part of the ciphertext.
Observe that, in this mode, no padding is necessary. If the length of the message
is not a multiple of the block length, the last block may be a partial block of length