Cryptography Reference
In-Depth Information
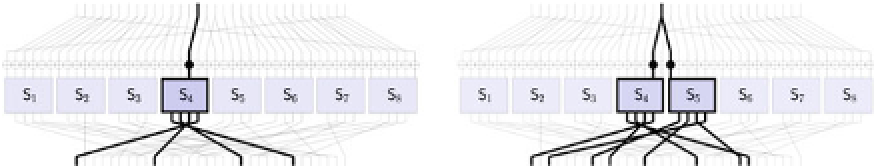
Fig. 3.5
Single-bit error propagation through the
f
-function with one active S-box (on the
left
)
and two active S-boxes (on the
right
)
Fig. 3.6
Error propagation on
round 15
Here, the round key
K
16
is not the only unknown value of the equation: the attacker
does not a priori know the error vector
or
at least to isolate it from among a small set of possible values. For such a purpose,
he shall use the XOR-difference
ε
. So the attacker has first to determine
ε
Δ
L
16
which satisfies
Δ
L
16
=
f
K
15
(
R
14
)
⊕
f
K
15
(
R
14
⊕
ε).
(3.4)
From this equation, one can deduce the active S-boxes in the 15th round. If two
S-boxes are active, then two solutions for
are possible since every pair of S-boxes
share at most two input bits (see Fig.
3.2
). If a single S-box is active then two solutions
are also possible that correspond to the input bits of the active S-box which does not
enter another S-box.
2
ε
2
Note that a one-bit differential in the input of a DES S-box cannot produce a zero differential in
the output.