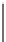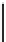Cryptography Reference
In-Depth Information
Fig. 2.2
A zero byte through the expansive permutation
bits known to be 0, we clearly see that
k
j
belongs to a set of only eight possible
values, which reveals three bits of information about the key.
Overall, the attack repeatedly tries to detect a plaintext producing such a rare pair
of related ineffective faults. As much information as possible is gathered by exploit-
ing this kind of event on every possible loci—defined by a couple (
xor_left
[
i
],
xor_key
[
j
])—at every round. According to simulation results, the median residual
entropy on the key is reduced from 56 to 26.49 bits (or 22.32 bits) after using 5
10
4
×
10
6
faults). The author also described an improved version of this attack
which gains information from more complex kinds of events. This improved attack
achieves a median residual entropy of 13.95 bits (or 6.68 bits) after using 5
faults (or 1
×
10
4
×
10
5
faults).
Compared to fault analysis on known cryptosystems, this attack requires a large
number of fault injections. This can be considered as a fair price to pay for the 'magic'
property of being able to retrieve the key of such unknown functions regardless of
the two secret external encodings
P
1
and
P
2
.
faults (or resp. 1
×
2.2.6 Passive and Active Combined Attacks on AES
The Boolean masking countermeasure that the two CFA attacks described above in
Sect.
2.2.4
can bypass is only intended to protect against first-order DPA. State-of-the-
art implementations must actually protect against high-order analyses, as introduced
by Messerges [284]. The basic principle of such a countermeasure is to use a Boolean
masking scheme based on one random byte that is different from one execution to
another (as is the case for a first-order countermeasure), also from one S-box operation
to another and from one round to another.
The recent attack presented by Clavier et al. in [94] actually succeeds in breaking
even this kind of protection. The state-of-the-art implementation considered by the
authors implements the S-box description from Oswald et al. [313] and is designed
to resist HO-DPA attacks such as those presented in [11, 270]. The method used
to break this implementation is a passive and active combined attack. The passive
part of the attack consists in an adaptation of Correlation Power Analysis (CPA),
originally described by Brier et al. [72]. As with the original analysis on unprotected