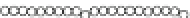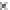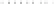Cryptography Reference
In-Depth Information
DES (16R)
DES (15R)
Camellia (18R)
Camellia (17R)
CAST128 (16R)
CAST128 (15R)
SEED (16R)
SEED (15R)
MISTY1 (8R)
MISTY1 (7R)
16
12
8
4
0
0
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
T
g
(ns)
Fig. 18.6
Average number of error bytes for other modules
Table 18.5
Calculated faulty intermediate values from correct and faulty outputs for the AES_SSS1
module
Round Correct output Faulty output Differences correct and
faulty outputs
Round 7
08e44dcc40a133bc\ 0a2242d42d5bace5\ 0000000000000000\
111388c26d693a71 f3b491a524d52ffd 0000007800000000
Round 8
47c65ea7b9a44b10\ 9b474f7630f607e4\ 0000000000000000\
c01bb154051bf7b7 3c102793f9c058dd 000000005454fca8
Round 9
4043e107f8740366\ 06f7df66a358f18a\ 5a5aeeb47e82fc7e\
73c9286d5fff1517 19cc5a54f91fe3af 84f87c7c06030305
Round 10
209b52ed447d30fa\ 163ce8530873138d\ d3c828782bd7445e\
1a8d0241ac46e8fe
e4265a286f9d5984
3e12a2b786637821
Key
000102030405060708c430b7323ba122
18.4.1.2 Interrelation Among the Position of Error Bits, Glitch Round,
and Glitch Width
T
g
In this section, we describe how the characteristics of a glitch change the number of
bits affected by its being injected into a given round with interval
T
g
. For example,
the results of the AES_PPRM1 module are shown in Fig.
18.8
a, b and c when the
fault injected into round 10 (the last round) and round 9. The points in these figures
represent the error occurrences in the output of round 9 or round 10 (ciphertext), and
the output bit in the bit position is different from that of the correct output. Each
graph is a result of 5,000 encryptions with various values for
T
g
. In these examples,
we randomly set the plaintexts and keys.
In these results, we can see many fragmented streaks of error bits. We believe that
the length of each streak largely corresponds to its path delay. In Fig.
18.8
a and b,
we can also see a similar trend in the fragmented streaks of error bit positions at the