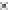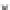Cryptography Reference
In-Depth Information
(a)
16
TBL (10R)
TBL (9R)
PPRM3 (10R)
PPRM3 (9R)
Comp_ENC_top (10R)
Comp_ENC_top (9R)
S (10R)
S (9R)
Comp (10R)
Comp (9R)
PPRM1 (10R)
PPRM1 (9R)
12
8
4
0
1
2
3
4
5
6
7
8
9
10
11
12
13
14
T
g
(ns)
(b)
16
AES_SSS1 (10R)
AES_SSS1 (9R)
12
8
4
0
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
T
g
(ns)
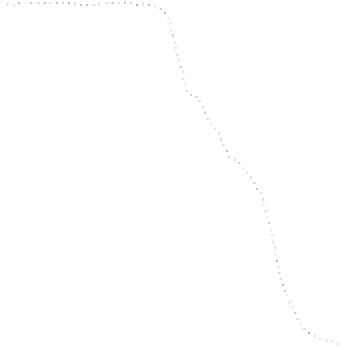
Fig. 18.5
Average number of error bytes for AES modules.
a
Results from AES module;
b
Results
from AES-SSS1 module
between the two intermediate states obtained by the correct and faulty ciphertexts
using the secret key we set with a PC. Table
18.5
compiles an example of the fault
propagation result, the values of the output of each round calculated from the correct-
faulty ciphertexts and secret key by computing the inverse operations of AES for the
AES_SSS1 module. This result shows that a one-byte fault can be injected into the
output of round 7, and a one-byte fault injected there is propagated to four bytes
in the next round's output by the MixColumns transformation.
1
The key retrieval
procedure will be discussed in Sect.
18.5.1
.
1
In order to inject faults into the output of round 7, we need to shorten
T
g
in round 8 in the case of
the AES_SSS1 module.