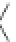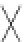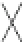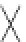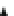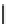Cryptography Reference
In-Depth Information
(a)
(n-1)
th
n
th
(n+1)
th
Cycle #
CLK
m
n-1
X (variable)
m
n
X (variable)
r_in
m
n-2
m
n-1
m
n
r_out
(b)
(n-1)
th
n
th
(n+1)
th
Cycle #
glitch
CLK
m
n-1
X (variable)
X (variable)
r_in
m
n-2
m
n-1
X (variable)
r_out
Fig. 18.2
Example waveforms of input and output from data resistor:
a
Normal operation
b
Glitch
occurs in clock signal during n-th cycle calculation
•
Control the switching timing by detecting the LSI execution using an oscilloscope
to change the time that a fault is injected, such as a particular round for block
ciphers.
•
Measure the actual shortened interval using an oscilloscope in order to collect
precise results.
We give the list of the equipment used in the experiments in Table
18.1
and an
overview of the developed experimental environment based on the above concepts
in Fig.
18.3
. A PC controls the cryptographic LSI and collects the results of faulty
calculations. An oscilloscope records the shortened interval of the clock for analysis.
The cryptographic LSI is mounted on a SASEBO-R board and controlled from a PC
via an FPGA on the evaluation board.
We developed an LSI controller in the FPGA written in Verilog HDL. This supplies
the LSI with a clock signal with a glitch, which is a combination of two external clocks
generated by a two-channel pulse generator. These two external clocks have the same
frequency but have different phases. The glitch is generated by changing the selection
of these clock sources at the appropriate point in time. To obtain the appropriate
timing, the glitch controller uses the Trigger_out signal of the oscilloscope, which
outputs a signal when it detects the EXEC signal of the LSI, which in turn outputs
the EXEC signal during the execution of the crypt calculation. Instead of using the
EXEC signal in the experiment, we can use a power consumption trace of the LSI by
setting a trigger using the characteristic form of a trace which appears in the execution