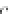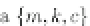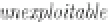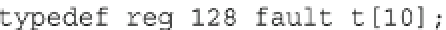Cryptography Reference
In-Depth Information
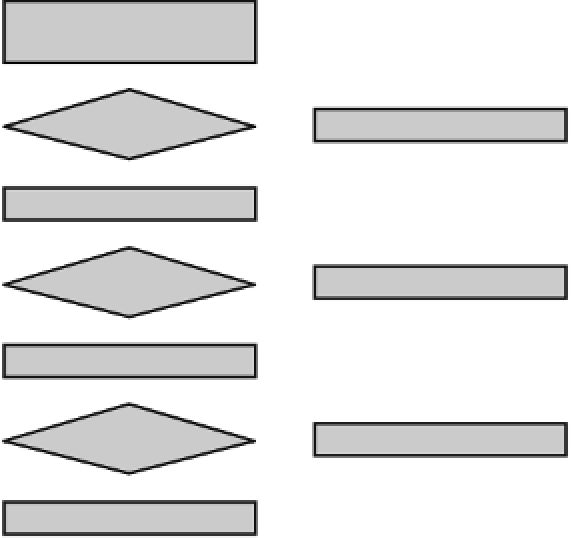
Fig. 17.6
AES-128 faults
analysis; in our research, the
value of
f
is zero, but for
exactly one byte
In this model we can see that the
f
value XORed with the message permits any
fault injection. The array
fault_t
is defined as:
where
reg_128
is typedef'ed for
char[4][4]
. The default value of the fault
f
,
aes_128::ZERO
, corresponds to 10
16 zeroes. To simulate a single-fault
injection, the
fault_t f
is initialized to all-zero, with the exception of a single
byte (
char
) within the
reg_128
state for a single round index. The fault analysis
consists in calling this function for all the possible fault values, and comparing
the output with the ciphertext obtained from the experimental platform. Indeed, the
only evidence that a fault has occurred experimentally is a faulted ciphertext. The
exhaustive search of single “byte-flip” requires
×
2
8
(
−
1
)
×
16
×
10
=
40,800 calls
to the “encrypt” routine. This allowed us to
•
find the experimental faulty ciphertext, in this case the fault is called “covered”, or
•
declare that the fault is “uncovered”, if the faulty ciphertext matches none of the
“encrypt” function results.
The purpose of this implementation is to identify the different types of faults that
occur in a smart card, as shown in Fig.
17.6
. In this figure, the AES function with
two arguments is the regular implementation of AES-128, whereas the AES function
with three arguments is the “encrypt” routine detailed previously.