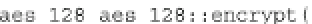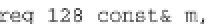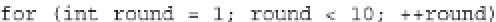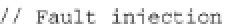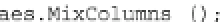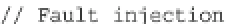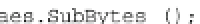Cryptography Reference
In-Depth Information
Fig. 17.5
Adapted encrypt function that computes AES with two arguments and a faulted AES
otherwise
know neither where nor when the errors occurred. However, to use this fault model
based on a “byte-flip”, a surgical fault injection is often carried out [379]. At the
opposite end we investigated a low-cost “global” fault injection technique based on
under-powering. This method is not surgical but rather “global” in the sense that the
whole algorithm is targeted simultaneously and continuously during the encryption
process. The voltage reduction allows the attacker to generate the single faults most
differential fault attacks are based on. The reason for this is that the stress caused by
the insufficient power supply remains gentle; dysfunctions do not appear suddenly
and thus complex multiple faults do not show up.
17.3.1.3 Analysis of Faults
In this section, we present an analysis of the two million results obtained from the
acquisition campaign described in Sect.
17.3.1.1
. In order to analyze the faults, we
assume that the message and the key are known to an attacker and that they are not
faulted. In other words, the faults concern only the computation of the encryption and
thus can affect only the ciphertext. We use a fast register transfer level (RTL) model
of the AES (“encrypt” function), adapted to corrupt any byte of the state matrix at
any round. The function is sketched in the C++ code snippet in Fig.
17.5
.