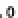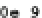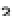Cryptography Reference
In-Depth Information
Fig. 17.3
SPICE simulation of the identical setup to Fig.
17.2
at nominal supply voltage, but where
the temperature varies in
150
◦
C
−
150
,
−
50
,
+
50
,
+
an integer multiplier, for which the most significant bit is much more critical than the
least significant bit. We note that the notion of critical path that we use is the dynamic
one rather than the static one. CAD tools compute the maximum frequency a circuit
can reach by evaluating a static metric; indeed, it is computationally impossible to
estimate a dynamic timing because of combinational explosion [380]. Therefore,
gates are modeled as nodes with delays and their interconnections are labeled with
estimated propagation times. A synthesizer looks for the critical path with an A
∗
like
algorithm, which happens to be the longest path in this netlist. However, in practice,
this path may not be activated, and other paths can become critical instead (albeit
with shortened timings). This accounts for the random repartitioning of global faults
in every register. When the stress gets stronger, multiple paths are violated simulta-
neously, which can cause double, triple or more faults located in one word (e.g. one
byte) or in several words.
Finally, we conclude with the suitability of global attacks to system-on-chips
(SoCs), even if they embed a wealth of coprocessors, such as control blocks and
device drivers, along with any cryptographic coprocessors. In such a complex, com-
pound system, it is not taken for granted that a global fault provokes a failure selec-
tively in one block. However, in practice, cryptographic modules are by far the most
computation-intensive, and therefore are very likely to host the critical path.