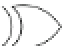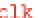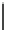Cryptography Reference
In-Depth Information
Fig. 17.1
Illustration of setup
violations when the clock
period is reduced below the
setup time
Setup met
Setup violated
D
Q
D
Q
Q'
Q'
path is also data-dependent. It is called the setup time and corresponds to the clock's
smallest admissible period.
If, for whatever reason, the clock period is less than the setup time, faults can
occur. This is illustrated in Fig.
17.1
: when either the clock accelerates or the data
signals decelerate, the setup time can be violated.
The slowdown of the logic gates when their supply voltage is reduced is illustrated
on a SPICE [301] simulation in Fig.
17.2
. This figure shows the voltage variation of
one bit from a combinational circuit that starts evaluating at
t
1 ns. The initial
value for this bit is “logical 1” and its final result is “logical 0” (0 V, i.e. the ground
potential). The transition between those two values is simulated for various supply
voltages, from the nominal 1
=
1 V. This voltage is
also present in the electrical value representing “logical 1”. We note that the time
needed for this bit to take its final value gets larger as the supply voltage is reduced.
Even for a supply voltage of 0
.
2V down to 0
.
4 V in steps of
−
0
.
4 V, close to the threshold of the transistors, the
gate output does not converge within a reasonable amount of time; the validity of the
simulation models is questionable under such extraordinary conditions. Nonetheless,
the effect of the supply voltage on the speed of evaluation is undebatable. Also, this
phenomenon is all the more important as the voltage is reduced.
More precisely, it can happen that the critical path is not activated, resulting in all
the signals being steady at the clock's rising edge. Consequently, no deviation from
normal behavior can be observed; but if the critical path is indeed violated then two
options are likely to be possible. Either the value of the longest path is sampled at
the rising edge of a clock as the correct value. In this case, the behavior is faulty,
but the result is correct by chance. Or the sampled value is the logical inverse of the
correct one, and the computation starts to be erroneous.
Figure
17.3
shows how the propagation delay is affected by the temperature of
the circuit. The same test bench used to generate the results in Fig.
17.2
is used, at
nominal voltage (1
.
.
2 V), but the temperature takes the values
−
150,
−
50,
+
50 and
150
◦
C. It is clear that the temperature has a smaller impact on the delay; thus,
underfeeding is a very effective means of fault injection.
Figures
17.2
and
17.3
show simulation results on a S-box, which is the most critical
resource in symmetric encryption algorithms, in terms of area and timing. This S-box
is made up of few gates (21 standard cells), which speeds up the computation, but it
is representative of any combinational block.
+