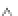Cryptography Reference
In-Depth Information
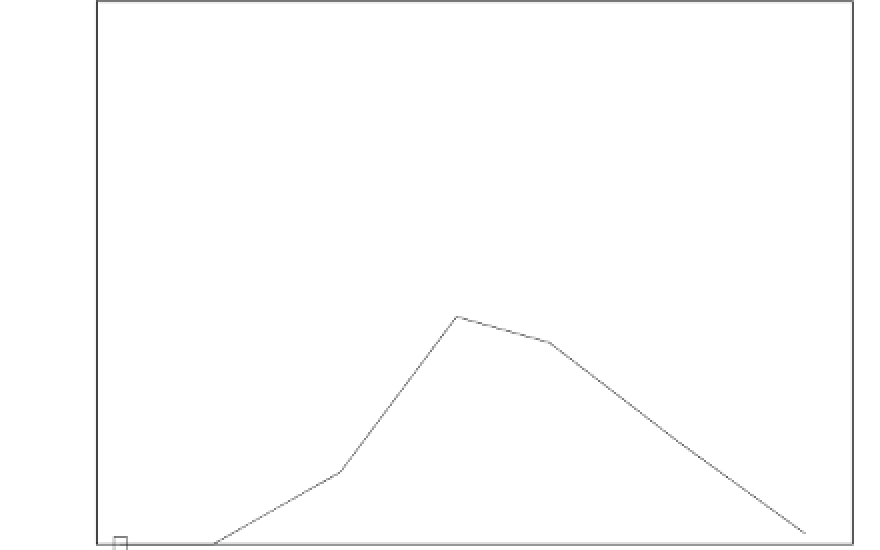
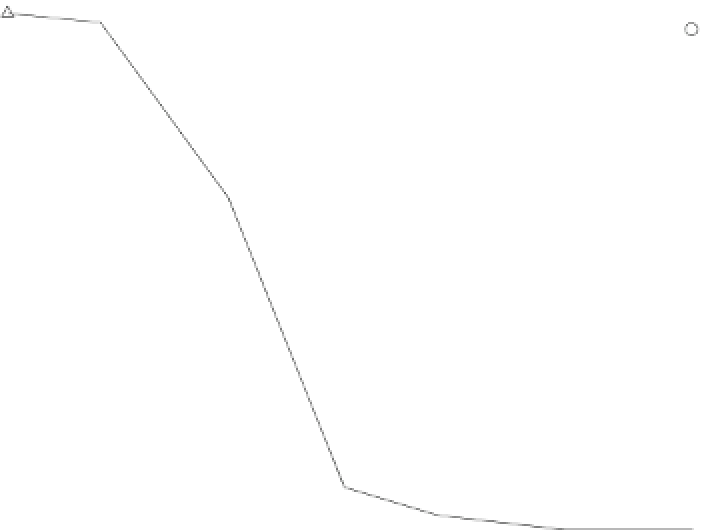
One Fault
Two Faults
Three or More Faults
100
80
60
40
20
0
905.5 906.0 906.5 907.0 907.5 908.0 908.5 909.0 909.5 910.0 910.5 911.0 911.5 912.0
Measured CPU Input Voltage [mV]
Fig. 16.4
Distribution of injected faults as a function of the voltage
to injecting single faults, as the fault incidence per single execution may be tuned
for binaries of different lengths by lowering or raising the voltage accordingly.
16.3.3 Fault Type Characterization
After ascertaining the possibility of injecting a single fault per computation, we
moved on to investigate what kind of fault has actually hit the computation by char-
acterizing its effect on the executed code.
By analyzing the binary at the assembly level, all the possible instructions executed
by a CPU may be split into three categories based on the architectural units composing
the CPU that are used to complete them. The three categories are arithmetic-logical
operations, memory reads and writes, and branch instructions. Since memory instruc-
tions represent the most expensive operation class in terms of power consumption,
they are expected to be the most vulnerable to underfeeding issues.
In order to validate this hypothesis, we recompiled the same probe program,
instructing the compiler to keep the variables in the CPU registers during the whole
computation, in order to avoid any memory operations while computing the result.
Only the instruction cache of the CPU was enabled, leaving only the data loading
operations uncached. The execution of the tuned program showed no faults, thus
indicating that the wrong values detected by the checks were uniquely to be ascribed