Cryptography Reference
In-Depth Information
8
Residue Mod 3
Hamming
Residue Mod 7
Parity
Double Parity
Complementary Parity
Reference
7
6
5
4
3
2
1
0
10
−7
10
−6
10
−5
10
−4
10
−3
10
−2
10
−1
10
0
Noise Standard Deviation [A]
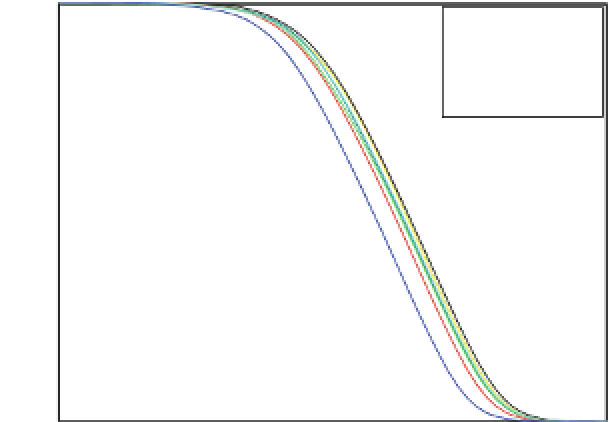
Fig. 15.8
Mutual information as a function of the noise's standard deviation for each of the con-
sidered error detection and correction codes
of the Hamming error correction code, there is a direct relation between the number
of check bits and the amount of information leakage. It is important to emphasize
that the ranking obtained using the information theory metric shows the number of
bits available to the strongest possible attacker; it is possible that in a specific attack
scenario in which the adversary is not able to exploit all the information present in the
power trace, the ranking of the circuits will be different. Still, this metric is the most
objective one since it does not depend on the specific attack hypothesis. In the next
section we show how the information stored in the power traces may be exploited by
an attacker who uses the correlation-based DPA and the Hamming weight model.
15.4.4 Evaluating the Effect of Check Bits on the Success Rate
The goal of the last set of experiments was to evaluate how the success rate of an
attacker who uses the correlation-based DPA varies for each different circuit as a
function of the power model used. We discuss in this section whether one of the
considered circuits is easier to attack than the others when the same attack is used.
Intuitively, the better the power model is, the easier it is for an adversary to recover
a key. One important result which can be obtained from these experiments is whether
the additional information leakage generated by the error detection/correction circuit
can be exploited by the attacker even if he is unaware of its existence.
To this end, we performed a set of correlation-based DPA attacks against all the
considered implementations of the AES S-box, using different attack hypotheses
and increasing at each run the number of traces. The attacks were performed using