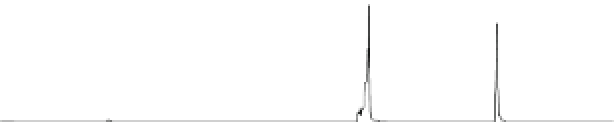Cryptography Reference
In-Depth Information
x
10
−4
2.5
2
1.5
1
0.5
0
−0.5
−1
−1.5
0
5,000
10,000
15,000
Time (ps)
Fig. 15.4
Kocher's DPA attack on the reference implementation of the AES S-box
x
10
−4
2.5
2
1.5
1
0.5
0
−0.5
−1
−1.5
−2
0
5,000
10,000
15,000
Time (ps)
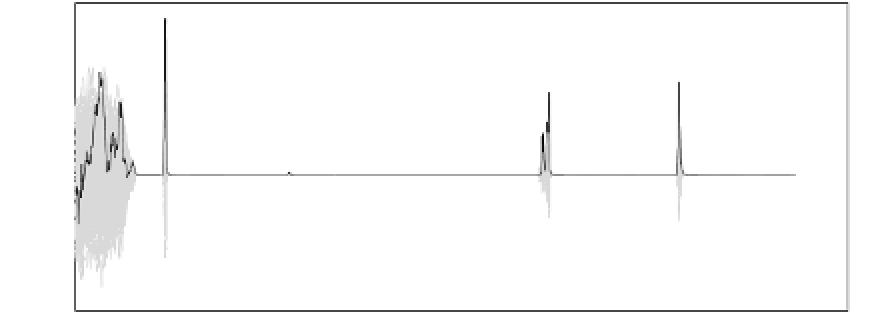
Fig. 15.5
Kocher's DPA attack on the implementation of the AES S-box with added complementary
parity
peak for the attacks on a check bit is approximately the same height as that for an
attack on an information bit. This shows that an attack on the parity bit is just as
efficient as an attack on any other bit. In contrast, when the selection bit does not
split the set evenly (as in the case of residue modulo 3 or 7), the strength of Kocher's
DPA attack is significantly reduced and it may even fail sometimes.
In summary, the experiments described above show that Kocher's DPA attacks
based on the difference of means and performed on noise-free traces are not sub-
stantially affected by the presence of an error detection circuit. Additionally, very
often the check bits can also be exploited by the attacker. Consequently, as a general
rule, when adding countermeasures against power analysis to an implementation that
includes an error detection circuit, the check bits should be protected as well.