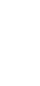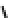Cryptography Reference
In-Depth Information
Fig. 15.1
Overview of the
considered part of the AES
algorithm
SecretKey
PointofAttack
PlainText
Substitution
Tabl e
Register
000000001
8
8
8
S-box
In
Out
9
Parity
Check
Parity
Check
9
9
1
1
Fig. 15.2
Block diagram of the parity error detection scheme applied to an eight-bit S-box
and the wrong ones is highest, and thus it is the preferred attack point for an adversary
[268]. Figure
15.1
depicts the basic configuration used in our experimental power
analysis attacks. This configuration is a commonly used simplified implementation
of one round of the AES cipher.
The plaintext is added (modulo 2) to the secret key and the result of this XOR
operation is used as input to the S-box. The output of the substitution step is stored in
a register. In order to always have the same initial condition, a reset signal is applied
to the register at the end of each write operation. Although a real implementation
of the full algorithm would be somewhat different from this simplified sketch, our
purpose is only to estimate the impact of error detection circuits (concatenated to
the S-box) on the resistance to power analysis attacks. This approximation (shown
in Fig.
15.1
) is accepted as sufficiently accurate for analyzing attacks on the most
vulnerable portion of the cipher and is therefore adequate for our needs.
Figure
15.2
shows, as an example, an S-box with a parity bit. In this figure, the
added check bits are used to detect the presence of errors in two different instances:
once at the input and then at the output of the S-box. When new data enters the S-box,
the check bits are separated from the data bits and an error detection is performed.
If no error is detected, the data bits enter the S-box circuit. The S-box then produces
the result of the non-linear transformation plus the corresponding check bits. At
this point the second check is performed, again as described before. If no error is
detected in both checks, the output of the S-box is forwarded to the next round
transformation; otherwise, a faulty output composed of all zeros except for the right
most bit is generated to signal the error.
We have implemented several versions of the nonlinear function in the AES S-box,
each with a different error detection or correction code. The following circuits are
considered: