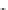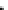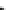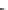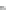Cryptography Reference
In-Depth Information
d
x1
x2
y1
y2
z1
z2
x1
x2
y1
y2
z1
z2
w
w
w
w
w
w
Predictor
<<
<<
y3
x3
z3
z3
y3
x3
w
w
w
EDN
Error
==
^2
^2
^2
Error
==
E
rror
==
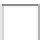
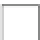
Fig. 11.12
Secure Edwards projective unified point addition
2
Z
1
Z
2
−
2
X
3
w
=
(
X
3
)
=[
Z
1
Z
2
(
X
1
Y
2
+
Y
1
X
2
)(
dX
1
X
2
Y
1
Y
2
)
]
,
2
Z
1
Z
2
+
2
Y
3
w
=
(
Y
3
)
=[
Z
1
Z
2
(
Y
1
Y
2
−
X
1
X
2
)(
dX
1
X
2
Y
1
Y
2
)
]
,
2
Z
1
Z
2
−
Z
1
Z
2
+
2
Z
3
w
=
(
Z
3
)
=[
(
dX
1
X
2
Y
1
Y
2
)(
dX
1
X
2
Y
1
Y
2
)
]
.
Next, we express the terms on the right-hand side as a function of the inputs and
their checksums. As an example, we show how to achieve this for
X
3
.Thesame
method can also be applied to the
Y
and
Z
coordinates as well.
Z
1
Z
2
−
2
X
3
w
=[
Z
1
Z
2
(
X
1
Y
2
+
Y
1
X
2
)(
dX
1
X
2
Y
1
Y
2
)
]
Z
1
Z
2
(
X
1
Y
2
Y
1
X
2
+
Z
1
Z
2
−
2
Z
1
Z
2
dX
1
X
2
Y
1
Y
2
=
+
2
X
1
Y
2
Y
1
X
2
)(
d
2
X
1
X
2
Y
1
Y
2
)
+
Z
1
w
Z
2
w
−
=
Z
1
w
Z
2
w
(
X
1
w
Y
2
w
+
Y
1
w
X
2
w
+
2
α)(
2
Z
1
w
Z
2
w
d
α
d
2
X
1
w
X
2
w
Y
1
w
Y
2
w
),
+
α
=
where
X
1
X
2
Y
1
Y
2
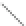
. After some algebra, we get the following equation array
for each coordinate of the resulting point
P
3. These equations mainly represent the
function implemented by the predictor unit in our design.