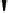Cryptography Reference
In-Depth Information
RFID tags or other pervasive computing applications that are extremely power or
cost constrained. (One of the topic authors participated in the design of PRESENT.)
!
Fig. 3.20
Internal structure and pseudocode of the block cipher PRESENT
Unlike DES, PRESENT is not based on a Feistel network. Instead it is a
substitution-permutation network (SP-network) and consists of 31 rounds. The
block length is 64 bits, and two key lengths of 80 and 128 bits are supported.
Each of the 31 rounds consists of an XOR operation to introduce a round key
K
i
for 1
32, where
K
32
is used after round 31, a nonlinear substitution layer
(sBoxLayer) and a linear bitwise permutation (pLayer). The nonlinear layer uses a
single 4-bit S-box
S
, which is applied 16 times in parallel in each round. The key
schedule generates 32 round keys from the user supplied key. The encryption rou-
tine of the cipher is described in pseudocode in Fig. 3.20, and each stage is now
specified in turn.
addRoundKey
≤
i
≤
At the beginning of each round, the round key
K
i
is XORed to the
current
STATE
.
sBoxlayer
PRESENT uses a single 4-bit to 4-bit S-box. This is a direct conse-
quence of the pursuit of hardware efficiency, since such an S-Box allows a much
more compact implementation than, e.g., an 8-bit S-box. The S-box entries in hex-
adecimal notation are given in Table 3.14.
Table 3.14
The PRESENT S-box in hexadecimal notation
x
0 1 2 3 4 5 6 7 8 9 A B C D E F
S
[
x
]
C 5 6 B 9 0 A D 3 E F 8 4 7 1 2
The 64 bit data path
b
63
...
b
0
is referred to as
state
. For the sBoxLayer the cur-
rent state is considered as sixteen 4-bit words
w
15
...
w
0
, where
w
i
=
b
4
∗
i
+3
||
b
4
∗
i
+2
||
b
4
∗
i
+1
||
b
4
∗
i
for 0
≤
i
≤
15, and the output are the 16 words
S
[
w
i
].