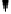Cryptography Reference
In-Depth Information
k
64
PC − 1
56
k
PC − 2
C
D
16
16
16
48
56
28
28
Transform 1
RS
RS
1
1
28
28
C
D
k
PC − 2
15
15
15
48
56
28
28
RS
RS
2
2
RS
RS
15
15
C
D
k
PC − 2
1
1
1
48
56
Fig. 3.16
Reversed key schedule for decryption of DES
Note that all variables in the decryption routine are marked with the superscript
d
, whereas the encryption variables do not have superscripts. The derived equation
simply says that the input of the first round of decryption is the output of the last
round of encryption because final and initial permutations cancel each other out. We
will now show that the first decryption round reverses the last encryption round. For
this, we have to express the output values (
L
1
,
R
1
) of the first decryption round 1
in terms of the input values of the last encryption round (
L
15
,
R
15
) . The first one is
easy:
L
1
=
R
0
=
L
16
=
R
15
We now look at how
R
1
is computed:
R
1
=
L
0
⊕
f
(
R
0
,
k
16
)=
R
16
⊕
f
(
L
16
,
k
16
)
R
1
=[
L
15
⊕
f
(
R
15
,
k
16
)]
⊕
f
(
R
15
,
k
16
)
R
1
=
L
15
⊕
[
f
(
R
15
,
k
16
)
⊕
f
(
R
15
,
k
16
)] =
L
15
The crucial step is shown in the last equation above: An identical output of the
f
-function is XORed twice to
L
15
. These operations cancel each other out, so that