Cryptography Reference
In-Depth Information
Key
k
Plaintext
x
64
64
PC−1
Initial Permutation
IP(x)
56
L
R
0
0
32
32
48
Transform 1
32
k
f
1
Round 1
32
56
L
R
1
1
L
R
15
15
32
32
48
Transform 16
32
k
f
16
Round 16
32
L
R
16
16
Final Permutation
−1
IP ( )
Ciphertext
y =
DES ( )
k
x
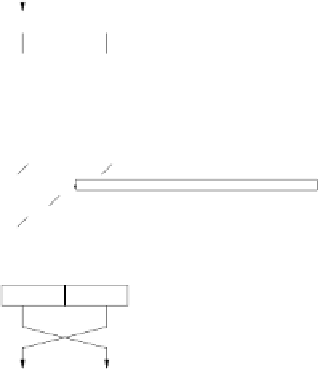
Fig. 3.5
The Feistel structure of DES
The two aforementioned basic properties of ciphers, i.e., confusion and diffusion,
are realized within the
f
-function. In order to thwart advanced analytical attacks,
the
f
-function must be designed extremely carefully. Once the
f
-function has been
designed securely, the security of a Feistel cipher increases with the number of key
bits used and the number of rounds.
Before we discuss all components of DES in detail, here is an algebraic descrip-
tion of the Feistel network for the mathematically inclined reader. The Feistel struc-
ture of each round bijectively maps a block of 64 input bits to 64 output bits (i.e.,
every possible input is mapped uniquely to exactly one output, and vice versa). This
mapping remains bijective for some arbitrary function
f
, i.e., even if the embedded
function
f
is not bijective itself. In the case of DES, the function
f
is in fact a sur-