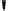Cryptography Reference
In-Depth Information
Fig. 2.4
Encryption and decryption with stream ciphers
2. Why can we use a simple modulo 2 addition as encryption?
3. What is the nature of the key stream bits
s
i
?
The following discussion of these three items will give us already an understanding
of some important stream cipher properties.
Why Are Encryption and Decryption the Same Function?
The reason for the similarity of the encryption and decryption function can easily
be shown. We must prove that the decryption function actually produces the plain-
text bit
x
i
again. We know that ciphertext bit
y
i
was computed using the encryption
function
y
i
≡
x
i
+
s
i
mod 2. We insert this encryption expression in the decryption
function:
d
s
i
(
y
i
)
≡
y
i
+
s
i
mod 2
≡
(
x
i
+
s
i
)+
s
i
mod 2
≡
x
i
+
s
i
+
s
i
mod 2
≡
x
i
+ 2
s
i
mod 2
≡
x
i
+ 0mod 2
≡
Q
.
E
.
D
.
x
i
mod 2
The trick here is that the expression (2
s
i
mod
2) has always the value zero since
2
0 mod 2. Another way of understanding this is as follows: If
s
i
has either the
value 0, in which case 2
s
i
= 2
≡
·
0
≡
0 mod 2. If
s
i
= 1, we have 2
s
i
= 2
·
1 = 2
≡
0 mod 2.
Why Is Modulo 2 Addition a Good Encryption Function?
A mathematical explanation for this is given in the context of the One-Time Pad in
Sect. 2.2.2. However, it is worth having a closer look at addition modulo 2. If we do
arithmetic modulo 2, the only possible values are 0 and 1 (because if you divide by
2, the only possible remainders are 0 and 1). Thus, we can treat arithmetic modulo
2 as Boolean functions such as AND gates, OR gates, NAND gates, etc. Let's look
at the truth table for modulo 2 addition:
This should look familiar to most readers: It is the truth table of the
exclusive-OR
,
also called
XOR
, gate. This is in important fact:
Modulo 2 addition is equivalent to