Cryptography Reference
In-Depth Information
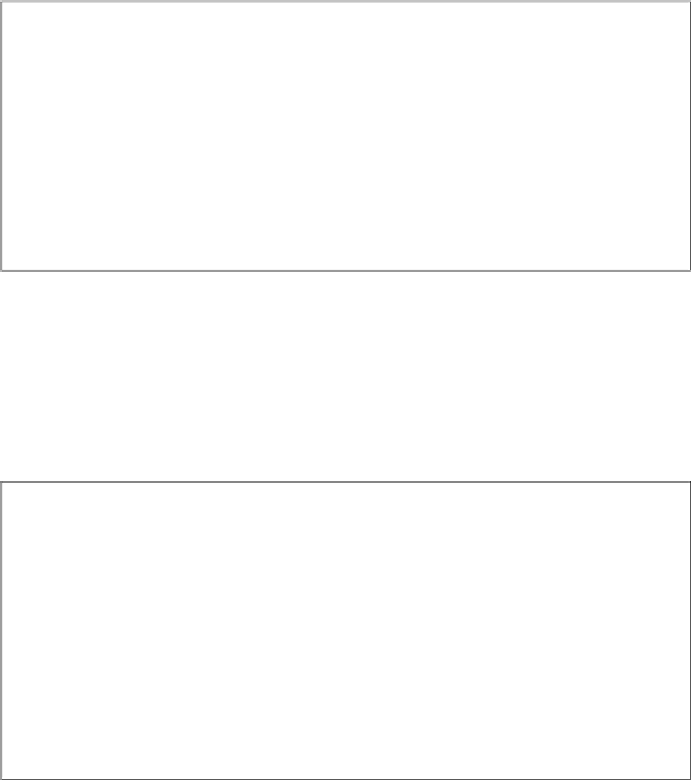
Diffie-Hellman Key Exchange
Alice
Bob
choose random
a
=
k
pr
,
A
choose random
b
=
k
pr
,
B
a
b
compute
A
=
k
pub
,
A
≡
α
mod
compute
B
=
k
pub
,
B
≡
α
mod
p
p
A
−−−−−−−−−−−−→
B
←−−−−−−−−−−−−
B
a
A
b
k
AB
≡
mod
p
k
AB
≡
mod
p
As we discussed in Sect. 8.4, if the parameters are chosen carefully, which in-
cludes especially a prime
p
with a length of 1024 or more bit, the DHKE is secure
against eavesdropping, i.e., passive attacks. We consider now the case that an adver-
sary is not restricted to only listening to the channel. Rather, Oscar can also actively
take part in the message exchange by intercepting, changing and generating mes-
sages. The underlying idea of the MIM attack is that Oscar replaces both Alice's
and Bob's public key by his own. The attack is shown here:
Man-in-the-Middle Attack Against the DHKE
Alice
Oscar
Bob
choose
a
=
k
pr
,
A
choose
b
=
k
pr
,
B
a
b
A
=
k
pub
,
A
≡
α
mod
B
=
k
pub
,
B
≡
α
mod
p
p
A
−−−−−−→
−−−−−−→
substitute
A
A
o
≡
α
B
←−−−−−−
substitute
B
B
←−−−−−−
o
≡
α
(
B
)
a
A
o
(
A
)
b
k
AO
≡
mod
p
k
AO
≡
mod
p
k
BO
≡
mod
p
B
o
k
BO
≡
mod
p
Let's look at the keys that are being computed by the three players, Alice, Bob
and Oscar. The key Alice computes is:
k
AO
=(
B
)
a
o
)
a
oa
mod
p
≡
(
α
≡
α
which is identical to the key that Oscar computes as
k
AO
=
A
o
a
)
o
ao
mod
p
.
≡
(
α
≡
α
At the same time Bob computes:
k
BO
=(
A
)
b
o
)
b
ob
mod
p
≡
(
α
≡
α
which is identical to Oscar's key
k
BO
=
B
o
bo
mod
p
. Note that the two
malicious keys that Oscar sends out,
A
and
B
, are in fact the same values. With use
different names here merely to stress the fact that Alice and Bob assume that they
have received each other's public keys.
b
)
o
≡
(
α
≡
α