Cryptography Reference
In-Depth Information
12.1 Principles of Message Authentication Codes
Similar to digital signatures, MACs append an authentication tag to a message. The
crucial difference between MACs and digital signatures is that MACs use a sym-
metric key
k
for both generating the authentication tag and verifying it. A MAC is a
function of the symmetric key
k
and the message
x
. We will use the notation
m
= MAC
k
(
x
)
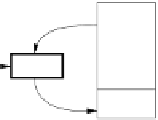
for this in the following. The principle of the MAC calculation and verification is
shown in Figure 12.1.
Alice
Bob
x
MAC
k
m
( , )
x m
x
MAC
k
m'
verification:
m = m'
?
Fig. 12.1
Principle of message authentication codes (MACs)
The motivation for using MACs is typically that Alice and Bob want to be assured
that any manipulations of a message
x
in transit are detected. For this, Bob computes
the MAC as a function of the message and the shared secret key
k
. He sends both
the message and the authentication tag
m
to Alice. Upon receiving the message
and
m
, Alice verifies both. Since this is a symmetric set-up, she simply repeats the
steps that Bob conducted when sending the message: She merely recomputes the
authentication tag with the received message and the symmetric key.
The underlying assumption of this system is that the MAC computation will yield
an incorrect result if the message
x
was altered in transit. Hence,
message integrity
is
provided as a security service. Furthermore, Alice is now assured that Bob was the
originator of the message since only the two parties with the same secret key
k
have
the possibility to compute the MAC. If an adversary, Oscar, changes the message
during transmission, he cannot simply compute a valid MAC since he lacks the
secret key. Any malicious or accidental (e.g., due to transmission errors) forgery of
the message will be detected by the receiver due to a failed verification of the MAC.