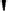Cryptography Reference
In-Depth Information
five working registers of size of 32 bits
A
,
B
,
C
,
D
,
E
a hash value
H
i
consisting of five 32-bit words
H
(0)
i
,
H
(1)
i
,
H
(2)
i
,
H
(3)
i
,
H
(4)
i
.Inthe
beginning, the hash value holds the initial value
H
0
, which is replaced by a new
hash value after the processing of each single message block. The final hash value
H
n
is equal to the output
h
(
x
) of SHA-1.
H
i−1
160
x
message
schedule
A
B
C
D
E
2560
W ... W
stage 1 (20 rounds)
0 19
f , K , W
1 1
0...19
A
B
C
D
E
W ... W
stage 2 (20 rounds)
20 39
f , K , W
2 2
20...39
A
B
C
D
E
W ... W
stage 3 (20 rounds)
40 59
f , K , W
3 3
40...59
A
B
C
D
E
W ... W
stage 4 (20 rounds)
60 79
f , K , W
4 4
60...79
32
addition mod 2
160
H
i
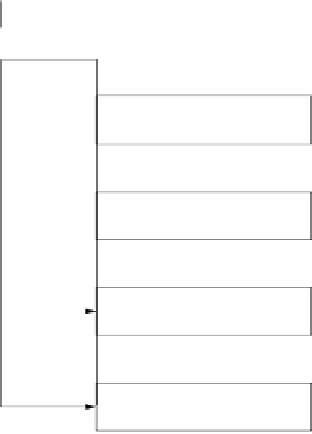
Fig. 11.11
Eighty-round compression function of SHA-1
The four SHA-1 stages have a similar structure but use different internal func-
tions
f
t
and constants
K
t
, where 1
4. Each stage is composed of 20 rounds,
where parts of the message block are processed by the function
f
t
together with
some stage-dependent constant
K
t
. The output after 80 rounds is added to the input
value
H
i
−
1
modulo 2
32
in word-wise fashion.
≤
t
≤