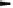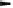Cryptography Reference
In-Depth Information
not get into the hands of their competitors, or of foreign intelligence agencies for
that matter.
Fig. 1.4
Communication over an insecure channel
In this situation, symmetric cryptography offers a powerful solution: Alice en-
crypts her message
x
using a symmetric algorithm, yielding the ciphertext
y
.Bob
receives the ciphertext and decrypts the message. Decryption is, thus, the inverse
process of encryption (Fig. 1.5). What is the advantage? If we have a strong encryp-
tion algorithm, the ciphertext will look like random bits to Oscar and will contain
no information whatsoever that is useful to him.
Fig. 1.5
Symmetric-key cryptosystem
The variables
x
,
y
and
k
in Fig. 1.5 are important in cryptography and have special
names:
x
is called
plaintext
or
cleartext
,
y
is called
ciphertext
,
k
is called the
key
,
the set of all possible keys is called the
key space
.
The system needs a secure channel for distribution of the key between Alice
and Bob. The secure channel shown in Fig. 1.5 can, for instance, be a human who
is transporting the key in a wallet between Alice and Bob. This is, of course, a
somewhat cumbersome method. An example where this method works nicely is
the pre-shared keys used in Wi-Fi Protected Access (WPA) encryption in wireless