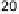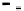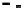Cryptography Reference
In-Depth Information
formed. If an exponent bit has the value 1, a squaring together with a multiplication
is computed. But this timing behavior reveals immediately the key: A long period
of activity corresponds to the bit value 1 of the secret key, and a short period to a
key bit with value 0. As shown in the figure, by simply looking at the power trace
we can identify the secret exponent. Thus we can learn the following 12 bits of the
private key by looking at the trace:
operations:
S SM SM S SM S S SM SM SM S SM
private key:
0
1
1
0
1
0 0
1
1
1
0
1
Obviously, in real-life we can also find all 1024 or 2048 bits of a full private key.
During the short periods with low activity, the square-and-multiply algorithm scans
and processes the exponent bits before it triggers the next squaring or squaring-and-
multiplication sequence.
Fig. 7.4
The power trace of an RSA implementation
This specific attack is classified as simple power analysis or SPA. There are sev-
eral countermeasures available to prevent the attack. A simple one is to execute a
multiplication with dummy variables after a squaring that corresponds to an expo-
nent bit 0. This results in a power profile (and a run time) which is independent
of the exponent. However, countermeasures against more advanced side-channel at-
tacks are not as straightforward.