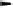Cryptography Reference
In-Depth Information
Fig. 5.7
Encryption and decryption in counter mode
the two plaintexts that were encrypted with the same input, he can compute the key
stream block and thus immediately decrypt the other ciphertext. In order to achieve
this uniqueness, often the following approach is taken in practice. Let's assume a
block cipher with an input width of 128 bits, such as an AES. First we choose
an IV that is a nonce with a length smaller than the block length, e.g., 96 bits.
The remaining 32 bits are then used by a counter with the value
CT R
which is
initialized to zero. For every block that is encrypted during the session, the counter
is incremented but the IV stays the same. In this example, the number of blocks we
can encrypt without choosing a new IV is 2
32
. Since every block consists of 8 bytes,
a maximum of 8
2
32
= 2
35
bytes, or about 32 Gigabytes, can be encrypted before
a new IV must be generated. Here is a formal description of the Counter mode with
a cipher input construction as just introduced:
×
Definition 5.1.5
Counter mode (CTR)
Let e
()
be a block cipher of block size b, and let x
i
and y
i
be bit
strings of length b. The concatenation of the initialization value IV
and the counter CT R
i
is denoted by
(
IV
||
CT R
i
)
and is a bit string
of length b.
Encryption
:y
i
=
e
k
(
IV
||
CT R
i
)
⊕
x
i
,
i
≥
1
Decryption
:x
i
=
e
k
(
IV
||
CT R
i
)
⊕
y
i
,
i
≥
1
CT R
1
) does not have to be kept secret. It can, for
instance, be generated by Alice and sent to Bob together with the first ciphertext
block. The counter
CT R
can either be a regular integer counter or a slightly more
complex function such as a maximum-length LFSR.
One might wonder why so many modes are needed. One attractive feature of the
Counter mode is that it can be parallelized because, unlike the OFB or CFB mode, it
does not require any feedback. For instance, we can have two block cipher engines
running in parallel, where the first block cipher encrypts the counter value
CT R
1
and
the other
CT R
2
at the same time. When the two block cipher engines are finished,
the first engine encrypts the value
CT R
3
and the other one
CT R
4
, and so on. This
scheme would allow us to encrypt at twice the data rate of a single implementation.
Of course, we can have more than two block ciphers running in parallel, increasing
the speed-up proportionally. For applications with high throughput demands, e.g.,
Please note that the string (
IV
||