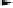Cryptography Reference
In-Depth Information
Fig. 5.1
Encryption and decryption in ECB mode
Definition 5.1.1
Electronic Codebook Mode (ECB)
Let e
()
be a block cipher of block size b, and let x
i
and y
i
be bit
strings of length b.
Encryption
:y
i
=
e
k
(
x
i
)
,
i
≥
1
Decryption
:x
i
=
e
−
1
(
y
i
)=
e
−
1
(
e
k
(
x
i
))
,
i
≥
1
k
k
It is straightforward to verify the correctness of the ECB mode:
e
−
1
k
(
y
i
)=
e
−
1
k
(
e
k
(
x
i
)) =
x
i
.
The ECB mode has advantages. Block synchronization between the encryption
and decryption parties Alice and Bob is not necessary, i.e., if the receiver does not
receive all encrypted blocks due to transmission problems, it is still possible to de-
crypt the received blocks. Similarly, bit errors, e.g., caused by noisy transmission
lines, only affect the corresponding block but not succeeding blocks. Also, block ci-
phers operating in ECB mode can be parallelized, e.g., one encryption unit encrypts
(or decrypts) block 1, the next one block 2, and so on. This is an advantage for
high-speed implementations, but many other modes such as the CFB do not allow
parallelization.
However, as is often the case in cryptography, there are some unexpected weak-
nesses associated with the ECB mode which we will discuss in the following. The
main problem of the ECB mode is that it encrypts highly deterministically. This
means that identical plaintext blocks result in identical ciphertext blocks, as long as
the key does not change. The ECB mode can be viewed as a gigantic code book —
hence the mode's name — which maps every input to a certain output. Of course, if
the key is changed the entire code book changes, but as long as the key is static the
topic is fixed. This has several undesirable consequences. First, an attacker recog-
nizes if the same message has been sent twice simply by looking at the ciphertext.
Deducing information from the ciphertext in this way is called
traffic analysis
.For
instance, if there is a fixed header that always precedes a message, the header always
results in the same ciphertext. From this, an attacker can, for instance, learn when
a new message has been sent. Second, plaintext blocks are encrypted independently
of previous blocks. If an attacker reorders the ciphertext blocks, this might result in
valid plaintext and the reordering might not be detected. We demonstrate two simple
attacks which exploit these weaknesses of the ECB mode.
The ECB mode is susceptible to
substitution attacks
, because once a particular
plaintext to ciphertext block mapping
x
i
→
y
i
is known, a sequence of ciphertext