Cryptography Reference
In-Depth Information
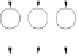
XOR operation is its own inverse, the key addition layer in the decryption mode is
the same as in the encryption mode: it consists of a row of plain XOR gates.
Key Addition
k
i
C
C
C
C
C
C
C
C
C
C
C
C
C
C
C
C
10
11
12
13
14
15
InvMixColumn
InvShiftRows
B
B
B
B
B
B
B
B
B
B
B
B
B
B
B
B
0
13
10
7
4
1
14
11
8
5
2
15
12
9
6
3
s
−1
s
−1
s
−1
s
−1
s
−1
s
−1
s
−1
s
−1
s
−1
s
−1
s
−1
s
−1
s
−1
s
−1
s
−1
s
−1
InvSubBytes
A
A
A
A
A
A
A
A
A
A
A
A
A
A
A
A
0
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
Fig. 4.9
AES decryption round function 1
,
2
,...,
n
r
−
1
Inverse MixColumn Sublayer
After the addition of the subkey, the inverse MixColumn step is applied to the state
(again, the exception is the first decryption round). In order to reverse the MixCol-
umn operation, the inverse of its matrix must be used. The input is a 4-byte column
of the State
C
which is multiplied by the inverse 4
4 matrix. The matrix contains
constant entries. Multiplication and addition of the coefficients is done in
GF
(2
8
).
×
⎛
⎞
⎛
⎞
⎛
⎞
B
0
B
1
B
2
B
3
0
E
0
B
0
D
09
09 0
E
0
B
0
D
0
D
09 0
E
0
B
0
B
0
D
09 0
E
C
0
C
1
C
2
C
3
⎝
⎠
⎝
⎠
⎝
⎠
=
The second column of output bytes (
B
4
,
B
5
,
B
6
,
B
7
) is computed by multiplying the
four input bytes (
C
4
,
C
5
,
C
6
,
C
7
) by the same constant matrix, and so on. Each value