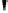Cryptography Reference
In-Depth Information
dition, the order of the subkeys is reversed, i.e., we need a reversed key schedule. A
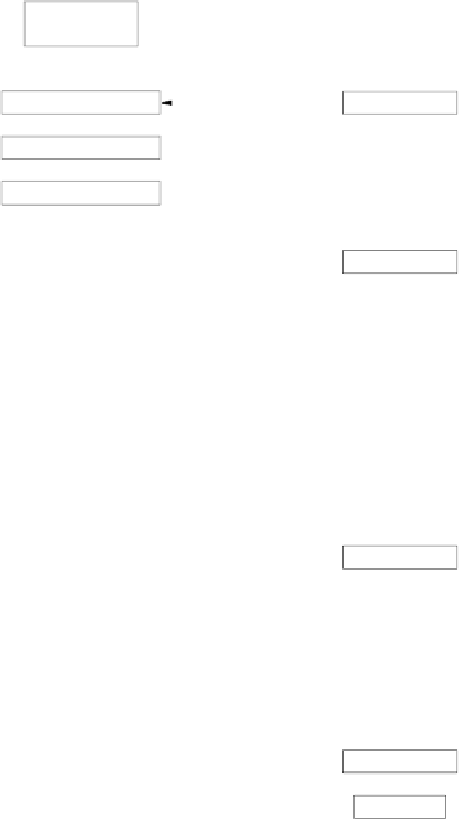
block diagram of the decryption function is shown in Fig. 4.8.
Ciphertext
y
k
n
r
Key Addition Layer
n
Transform
r
Inv ShiftRows Layer
inverse of round
n
r
Inv Byte Substitution
k
r
−1
n
Key Addition Layer
n
Transform −1
r
Inv MixColumn Layer
inverse of round −1
n
r
Inv ShiftRows Layer
Inv Byte Substitution
k
1
Key Addition Layer
Transform
1
Inv MixColumn Layer
inverse of round 1
Inv ShiftRows Layer
Inv Byte Substitution
k
0
Key Addition Layer
Transform
0
Key
k
Plaintext
−1
x=
AES ( )
y
Fig. 4.8
AES decryption block diagram
Since the last encryption round does not perform the MixColum operation, the
first decryption round also does not contain the corresponding inverse layer. All
other decryption rounds, however, contain all AES layers. In the following, we dis-
cuss the inverse layers of the general AES decryption round (Fig. 4.9). Since the