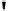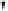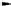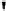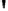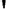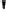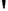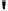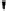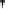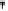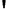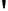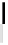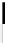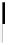Cryptography Reference
In-Depth Information
K
K
K
K
KKKKKKKKKKKKKKKKKKKKKKKKKKKK
31
30
0 123456789 0 1 2 3 4 5 6 7 8 9 0 1 2 3 4 5 6 7
28
29
32
32
32
32
32
32
32
32
W[0]
W[1]
W[2]
W[3]
W[4]
W[5]
W[6]
W[7]
g
h
W[8]
W[9]
W[10]
W[11]
W[12]
W[13]
W[14]
W[15]
W[48]
W[49]
W[50]
W[51]
W[52]
W[53]
W[54]
W[55]
g
function of round
g
i
−function
h
32
32
V
0
V
1
V
2
V
3
V
0
V
1
V
2
V
3
8
8
8
8
S
S
S
S
V
1
V
2
V
3
V
0
W[56]
W[57]
W[58]
W[59]
S
S
S
S
32
RC[i]
8
32
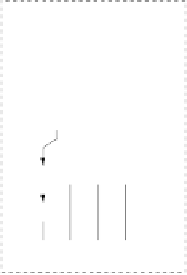
Fig. 4.7
AES key schedule for 256-bit key size
4.5 Decryption
Because AES is not based on a Feistel network, all layers must actually be in-
verted, i.e., the Byte Substitution layer becomes the Inv Byte Substitution layer,
the ShiftRows layer becomes the Inv ShiftRows layer, and the MixColumn layer
becomes Inv MixColumn layer. However, as we will see, it turns out that the inverse
layer operations are fairly similar to the layer operations used for encryption. In ad-