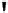Cryptography Reference
In-Depth Information
K
KKKKKKKKKKKK
0 123
32
K
K
K
456789 0 1 2 3 4 5
32
32
32
round key 0
W[0]
W[1]
W[2]
W[3]
g
function of round
g
i
32
round key 1
W[4]
W[5]
W[6]
W[7]
V
V
V
V
8
8
8
8
V
V
V
V
round key 9
W[36]
W[37]
W[38]
W[39]
S
S
S
S
g
RC[i]
8
32
round key 10
W[40]
W[41]
W[42]
W[43]
Fig. 4.5
AES key schedule for 128-bit key size
computed as follows. As can be seen in the figure, the leftmost word of a subkey
W
[4
i
], where
i
= 1
,...,
10, is computed as:
W
[4
i
]=
W
[4(
i
−
1)] +
g
(
W
[4
i
−
1])
.
Here
g
() is a nonlinear function with a four-byte input and output. The remaining
three words of a subkey are computed recursively as:
W
[4
i
+
j
]=
W
[4
i
+
j
−
1]+
W
[4(
i
−
1)+
j
]
,
where
i
= 1
,...,
10 and
j
= 1
,
2
,
3. The function
g
() rotates its four input bytes,
performs a byte-wise S-Box substitution, and adds a
round coefficient RC
to it. The
round coefficient is an element of the Galois field
GF
(2
8
), i.e, an 8-bit value. It is
only added to the leftmost byte in the function
g
(). The round coefficients vary from
round to round according to the following rule: