Cryptography Reference
In-Depth Information
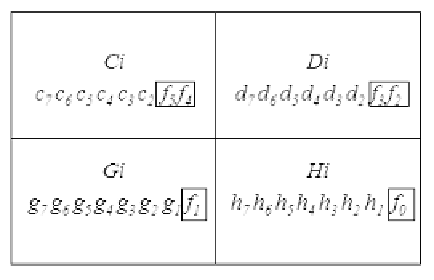
FIGURE 16.20
The four pixels of each cover block CBi.
Step 4:
To prevent illicit attempts, a simple authentication ability is
added here. Compute check bits pi by using Equation 16.17 and
embed pi into the remaining LSBs of Ci,
i
, D
i
, G
i
, H
i
from the
same cover block CBi,
i
, where i = 1, 2, ..., t. Note that t is the
total number of check bits, which is discretionary and could be
decided by the sender according to authentication strength. For
simplicity, we take t = 2 as an example to explain the procedure
as shown in
Figure 16.22.
Figure 16.23
illustrates a flowchart of
FIGURE 16.21
Hiding the six data bits of F(Xi).








Search WWH ::

Custom Search