Cryptography Reference
In-Depth Information
pixels listed below should be considered in distinguishing these cases.
Case 1: The pixels located at (x, 1), where x = 1, 2,..., H-1.
Case 2: The pixels located at (H, y), where y = 1, 2,... , W-1.
Case 3: The pixels located at (x, W), where x = 1, 2,..., H-1.
Case 4: The pixel located at (H, W).
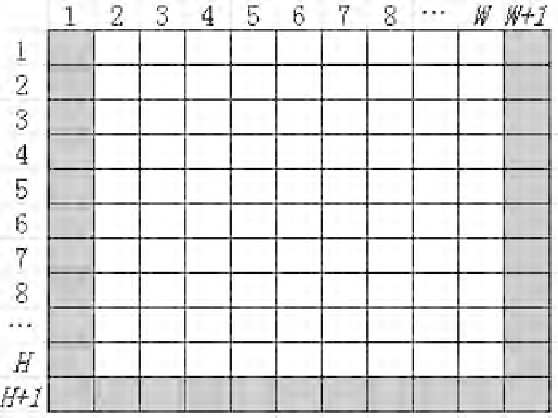
The positions of all four kinds of pixels are represented in Figure 16.9, with
the white squares showing the positions of the pixels located at the border
of an image. To deal with these special cases, we adopt a special skill, called
"excursion" in the procedure, as shown in
Figure 16.10.
FIGURE 16.9
The positions of pixels located at the border in an image.
When applied to these pixels, Floyd and Steinberg's error lter is slightly
modified to ignore the nonexistent pixels because the number of these pixels is
small compared with the total number of pixels in the whole image. To give a
clearer explanation, the following paragraphs give one instance for each case.
At first, set E(1, 1) = 0. For case 1, the pixels at position (x, 1), where x =
1, 2,..., H-1 are considered. We take the pixel at position (1, 1) for example.
The value of HI(1, 1) is determined by Equation 16.7. However, there is no
pixel at position (2, 0) corresponding to GI(x+1, y-1). Thus, the neighboring
pixels that accepted error diffusion are shown in
Figure 16.11
for Case 1.
For Case 2, we take the pixel at position (H, 1) for example. The pixel at
position (H, 1) is called GI(H, 1) and has an error value of E(H, 1). However,







Search WWH ::

Custom Search