Cryptography Reference
In-Depth Information
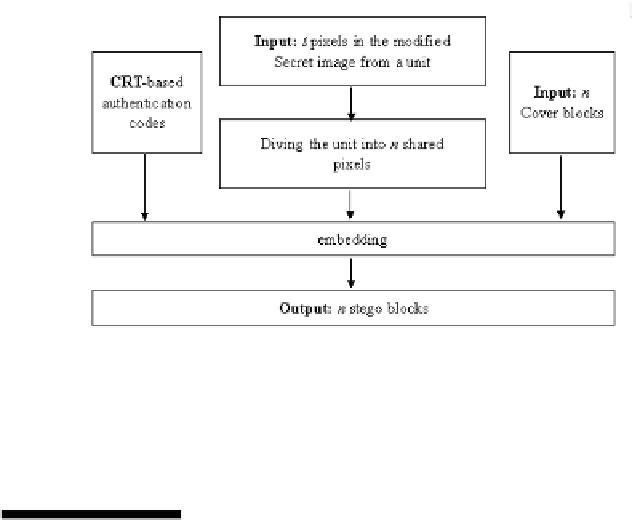
FIGURE 16.6
The owchart of Chang et al.'s scheme.
16.3 Adopted Techniques in the Proposed Scheme
To give sucient background knowledge, this section briefly introduces the
related techniques adopted in our proposed scheme, including error diffusion,
interpolation, canny edge detector, and edge lookup inverse halftoning as well
as the Shamir scheme for secret sharing, respectively.
16.3.1 Error Diffusion Technique
The error diffusion technique is typically used to convert a multiple-level color
image into a two-level color image. There are many kinds of idiographic error
diffusion strategies. The common concept behind diffusion is the diffusion
of errors to neighboring pixels; in this way, no image luminance is lost. The
diffused image generated based on an error diffusion strategy is called an error
filter. Each error filter has a set of kernel weights. Assume that GI(x,y) is the
value of a pixel in position (x,y) in a grayscale secret image.
Figure 16.7
is a
flowchart of the error diffusion technique.
In the proposed scheme, the Floyd and Steinberg error diffusion strategy is
adopted and the kernel weights are Wr =
7
5
3
1
16
;Wb =
16
;Wbl =
16
;Wbr =
16
,
as shown in
Figure 16.8.
After the quantization procedure, a pixel GI(x,y) at position (x,y) in
grayscale image GI becomes HI(x,y) and has a value of either 0 or 255. Dur-
ing the quantization procedure, a threshold TH is used to determine HI(x,y)
according to Equation 16.7 and the quantization error is determined by Equa-












Search WWH ::

Custom Search