Cryptography Reference
In-Depth Information
set to the Galois Field GF(2
8
), that is, p = g(x) = x
8
+ x
4
+ x
3
+ x
1
+ x
0
.
This approach allows the acquisition of a secret image without distortion.
FIGURE 16.3
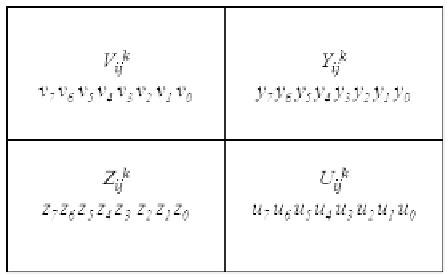
The cover blocks used in Yang et al.'s scheme.
FIGURE 16.4
The block of a stego-image in Yang et al.'s scheme.
In Yang et al's scheme, let the pixel I
ij
of the secret image be used to
produce the n shared pixels S
ij
, S
ij
,...,S
ij
, to be embedded into the cover
blocks C
ij
,C
ij
,...,C
ij
, where each cover block is represented as C
ij
= fV
ij
,
Y
ij
, Z
ij
, U
ij
g for 1 k n as shown in Figure 16.3. Pixel I
ij
of the secret
image is first embedded into the coecient c
0
to construct a polynomial as
shown in Equation 16.1. Next, the shared pixel S
ij
is computed by taking the
pixel value V
ij
of the corresponding cover image block C
ij
as the input x of
the polynomial shown in Equation 16.1. Let the binary representation of the
shared pixel S
ij
be (s
1
s
2
...s
8
). Hence, the shared pixel S
ij
is embedded into








Search WWH ::

Custom Search