Cryptography Reference
In-Depth Information
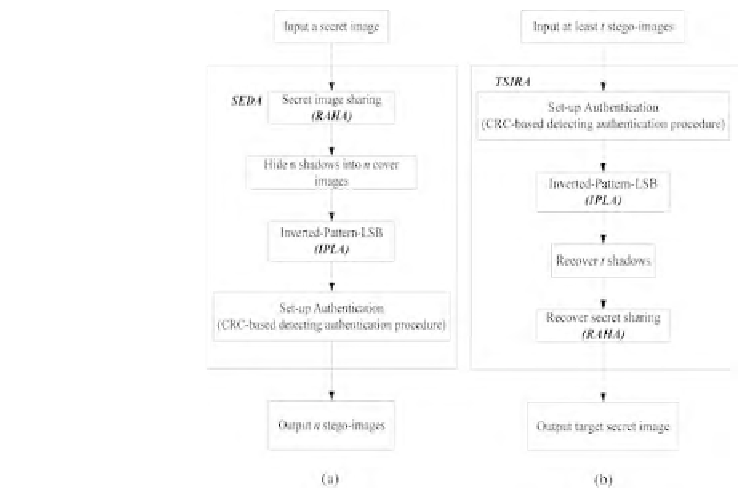
FIGURE 15.5
A secret sharing system with target secret embedding of high capacity and
detection authentication: (a) Flowchart of target secret embedding procedures;
(b) Recovery of target secret forms the stego-images in our secret sharing
systems.
B
g;j
= (x
51
; ;x
56
;y
g5
;c
g5
),
B
g;j
= (x
61
; ;x
66
;y
g6
;c
g6
),
B
g;j
= (x
71
; ;x
76
;y
g7
;c
g7
),
B
g;j
= (x
81
; ;x
86
;y
g8
;c
g8
),
gaining
l
m
2
t
m
blocks
I
j
by
B
g;j
in
Step 6. Construct
order, g =
1; 2; ;
l
m
2
t
m
.
Target Secret Image Recovery Algorithm: The TSIRA aims at the
recovery of the original secret image.
Input: A set of at least t stego-images and a secret key K.
Output: A target secret image S if all the stego-images are authenticated to
be genuine.
Step 1. Renumber t of the inputted stego-images as I
j
, j = 1; 2; ;t, in
order.






Search WWH ::

Custom Search