Cryptography Reference
In-Depth Information
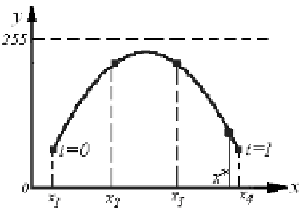
FIGURE 14.6
Image sharing scheme based on moving lines.
then P[t] = L
0
[t]L
1
[t], t 2 [0; 1] represents a rational Bezier curve of degree
p + q as shown in
Figure 14.5(b)
[16].
As in the case of Lagrange interpolation, we now construct the scheme of
image sharing based on moving lines as shown in Figure 14.6. In Figure 14.6,
the x-coordinate depicts the given position of the original secret color image,
the y-coordinate indicates the values of the gray-scale pixel value, t is the
parameter for moving lines generation, and x
is the position of the new
computed share. For image sharing, we compute the shares using the above
implicit curve. We now present the detailed steps for our moving lines based
on the color image sharing scheme.
Steps of sharing a color image:
1. Suppose we are given one secret image I
0
to be shared, k+ 1 images
I
0
;I
1
; ;I
k
as the innocuous images and a group of corresponding
parameters x
0
, x
1
,, x
k
(x
0
x
1
x
k
) as input;
2. Calculate an arbitrary new share corresponding to a parameter
within the interval of the given parameters (x
1
;x
k
);
3. The images (greater than k) I
0
, I
1
, , I
i1
, I
p
, I
i
,I
i+1
,, I
k
;
0 i 1 p i k and their corresponding parameters x
0
, x
1
,
, x
i1
, x
p
, x
i
, x
i+1
, , x
k
(x
0
x
1
x
i1
x
p
x
i
x
i+1
x
k
) are the output computed image shares.
Steps of reconstructing the color image:
1.
Select k image shares I
0
, I
1
, , I
k
and their corresponding position
parameters x
0
, x
1
, , x
k
(x
0
x
1
x
k
) and the position
parameter of the color image x
0
as the input;
2.
Calculate the implicit curve corresponding to pixels in each share
according to the moving lines scheme P[t] = L
0
[t]L
1
[t], t 2 [0; 1];
3.
Reconstruct the secret color image by the scheme of moving lines
at the position of x
0
as output.











Search WWH ::

Custom Search