Cryptography Reference
In-Depth Information
group of mutually suspicious individuals or processes need to cooperate and
every threshold subset of the group needs to be given the veto power.
The problem of color image sharing is formally defined as follows. In order
to transfer a color image I through a public channel securely, the information
of the color image is divided into n pieces and embedded into images Ii,
i
,
(i = 1; 2; ;n), and we call the images I
i
, (i = 1; 2; ;n) as shares. With
the knowledge of any k(k < n) shares I
i
, (i = 1; 2; ;k), the restoration of
the original color I image is easy; with the knowledge of any k 1(k < n)
shares, the restoration of the original image I is impossible (i.e., any image is
equally likely to be reconstructed).
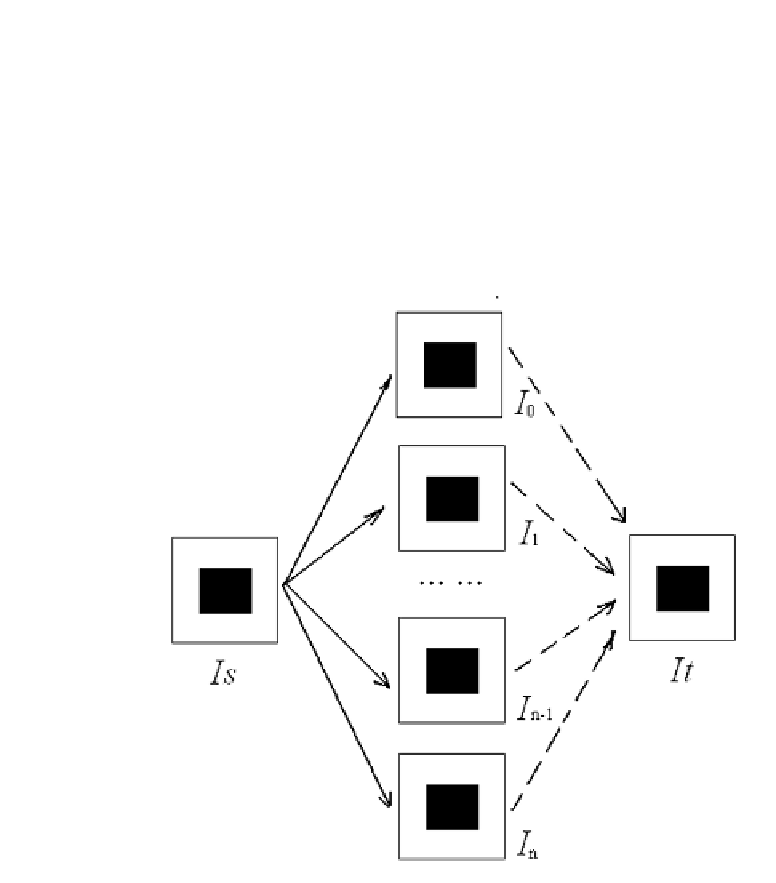
FIGURE 14.1
Principle of image sharing.
In Figure 14.1, the left-most image is the original color image that we
desire to keep as a secret and it is divided into several blocks (subimages). We
process each of these blocks into n shares in order to create the subimages
shares. If required, we can compose these shares I
i
, (i; = 1; 2; ;n) together
and compute the blocks in the right-most image. Block-based processing is
done for breaking correlation. Note that our scheme will require a minimum
of k shares in order for If
r
to be exactly equal to If
s
. If less than k shares are










Search WWH ::

Custom Search