Cryptography Reference
In-Depth Information
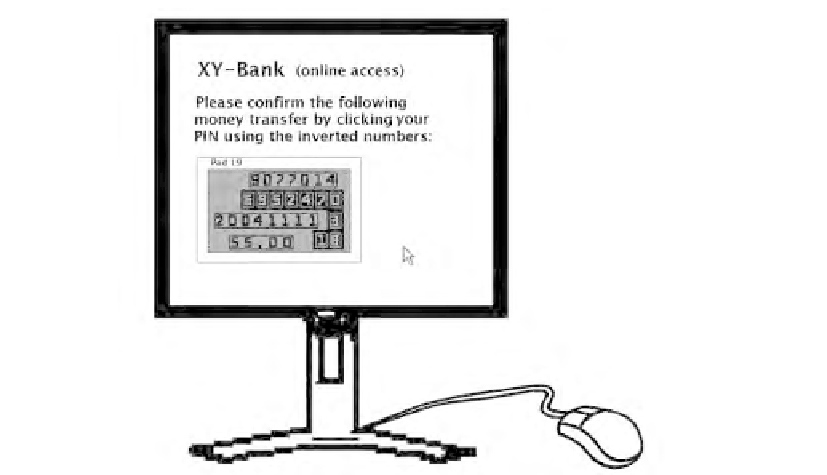
FIGURE 12.10
For confirmation, the user has to click his PIN using inverted numbers.
in which each subcluster has a 0 on the slide. To encrypt the i-th image, we
use only the i-th subcluster as above and fill the rest with 1. This leads to
a contrast of
nc
.
2. For one pixel use a cluster of c
n
pixels, which we address as an n-dimensional
array (but arrange 2-dimensionally). Only one pixel in each cluster has a 0
on the slide. To encrypt a pixel p 2 in the i-th image, place p at each
position of the cluster, which has the same i-th coordinate as the 0 on the
slide then choose a random permutation of nfpg and ll the rest of the
cluster in a way such that pixels with the same i-th coordinate get the same
color. This leads to a contrast of
1
c
n
.
In both cases each combination of images is consistent with any combina-
tion of encrypted images. In the first case, the contrast can be improved only
to
1
n
using refraction, whereas it can be improved to 1 using refraction in the
second case.
In the case of an unknown plaintext attack, Eve is still able to obtain the
secret images if the slide was used too often and if she can anticipate patterns
in the picture. Let us consider the simple case = f0; 1g, c = 2 and the slide
was used twice. Then Eve can XOR both encrypted images resulting in an
image that is 0 at pixels where both original images coincide and 1 at pixels
where both original images differ, thus she can see the difference of the original
pictures as shown in [12] page 35 and
Figure 12.11.
Now assume the original







Search WWH ::

Custom Search