Cryptography Reference
In-Depth Information
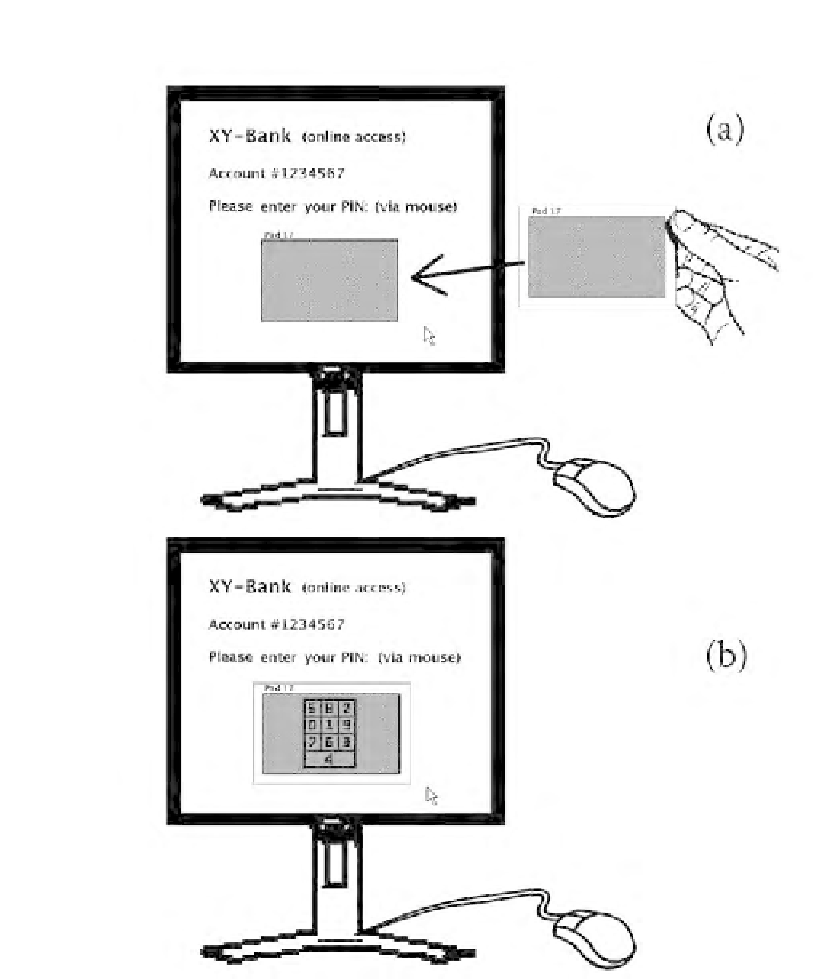
FIGURE 12.8
(a) To log in, the server sends an encrypted image of a permutated keyboard,
which the user can only read after placing the slide over it. (b) The user enters
the PIN by clicking at the positions according to their order in the PIN.






Search WWH ::

Custom Search