Cryptography Reference
In-Depth Information
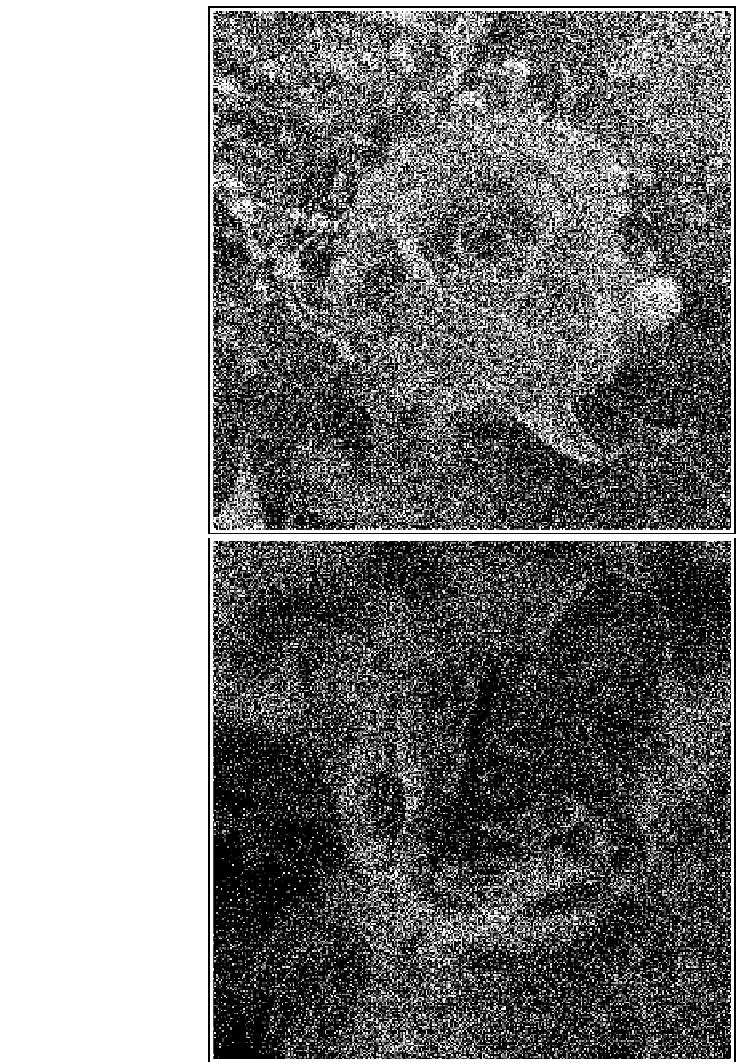
FIGURE 4.18
Examples of the output with density pattern using 3 3. The upper image is
the encrypted shadow 2 and the lower image is the secret image reconstructed
by superimposing the two shadows by computer simulation.






Search WWH ::

Custom Search