Cryptography Reference
In-Depth Information
0
8
2
10
8
0
10
2
12
4
14
6
4
12
6
14
3
11
1
9
11
3
9
1
15
7
13
5
7
15
5
13
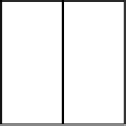
FIGURE 4.9
Dither matrices for similar shadow scheme proposed in [34].
subpixels, of the first shadow image if the corresponding original secret pixel
is black. On the contrary, the same arrangement is used if the corresponding
secret pixel is white. The secret image appears when the shadow images are
stacked together. It is easy to rearrange subpixels if the gray level of the orig-
inal pixel is approximately 50% gray. But it is dicult to control resulting
darkness in the nearly white or black region of the shadow image. Thus, it is
impossible to guarantee the quality of the reconstructed secret image.
[34, 21, 41] are modifications of this approach without pixel expansion,
namely, m = 1, by using ordered dither. For instance, [34] specified sample
dither matrices based on a Bayer's matrix as shown in Figure 4.9. Shadow im-
ages are halftoned by using the same dither matrix if the corresponding secret
region is white, while they are halftoned with the different dither matrices if
the corresponding secret region is black. Fu and Au proposed a variation of
this scheme in 2001 [9]. It uses the error diffusion technique to get halftoned
results instead of ordered dither.
4.4.4 Positive and Negative Shadow Images
The underlying concept of this approach is quite similar to the previous ap-
proach. It can achieve a large relative difference for shadow images by using a
positive and negative pair of shadow images instead of a similar pair. It also
reconstructs a logo or text image as a secret image, i.e., binary-tone image,
without any trace of shadow images.
This scheme was proposed by Zhou et al. in 2006 [47]. It is not limited
to (2; 2) VSSS and can handle an access structure. However, here we explain
a basic algorithm to establish a (2; 2) secret sharing scheme due to space
limitations.
1.
The positive shadow image is generated by halftoning the original
shadow image. The negative shadow image is obtained by reversing
the positive one. Thus, the overlapping result is entirely black at
this moment.
2.
A secret pixel is encrypted into a square region of halftoned pix-
els, Q
1
Q
2
. A pair of black and white pixels, referred to as secret
















Search WWH ::

Custom Search