Cryptography Reference
In-Depth Information
(a)
(b)
(c)
(d)
(e)
(f)
(g)
(h)
(i)
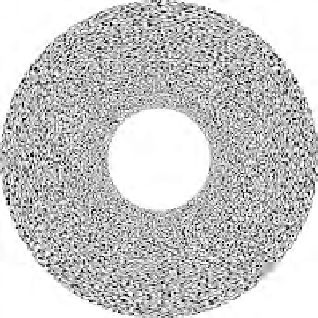
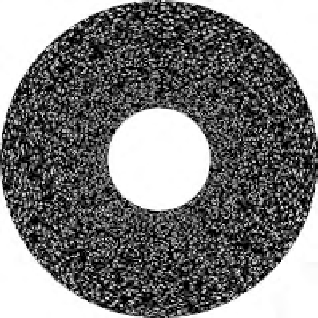
FIGURE 3.20
Implementation results for the proposed visual 3-secret sharing scheme: (a)
P
1
, (b) P
2
, (c) P
3
, (d) A, (e) B, (f) AB, (g) A
120
B, (h) A
240
B, (i)
A
85
B.













Search WWH ::

Custom Search