Database Reference
In-Depth Information
Figure 4-18
.
The system_auth keyspace described
2.
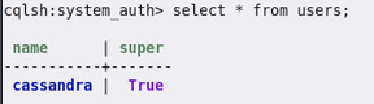
Let's explore the
users
table as shown in
Figure 4-19
.
Figure 4-19
.
Default user in the users table
3.
truncate users;
Figure 4-20
.
Truncated users table