Information Technology Reference
In-Depth Information
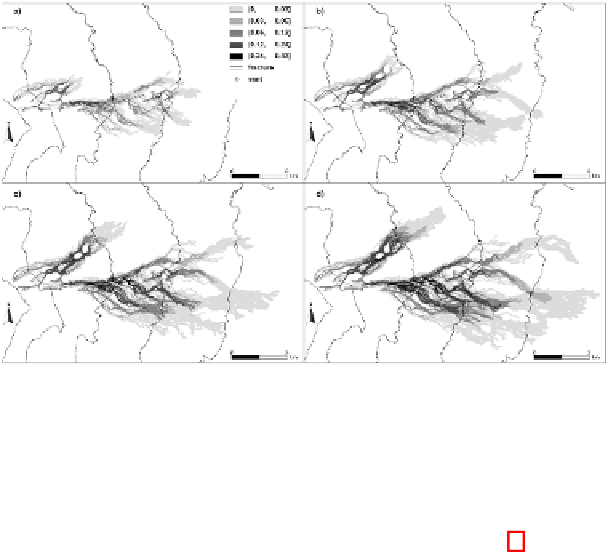
Fig. 6.
A hypothetical hazard scenario for a system of eruptive fissures propagating downslope
over a length of 7 km on the east-northeast flank of Mount Etna. The figure refers to lava hazard
of the area after 1, 3, 6 and 9 days (a, b, c, d), respectively. Note that the same scenarios can be
considered as temporal scenario for the area.
them selected from the simulation database (without needing to perform new simula-
tions). For this application, the resulting map is shown in Figure 6. The same figure
refers also to a further application regarding temporal hazard mapping, by evidencing
the evolution of the involved area in time. This application could be of fundamental
importance for assessing, from a temporal point of view, how hazard of a specific area
evolves in time (e.g. day by day), so that more specific countermeasures can be consid-
ered by responsible authorities.
In particular, Figure 6 also shows the result relative to 1, 3, 6 and 9 days respectively,
of the invaded areas, with relative probability values of occurrence, in the case of the
activation of the considered fissure system. This application regards a real-time assess-
ment of lava invasion in confined areas, since the produced map indicates a temporal
evolution of hazard, in terms of probability, which can be useful in case of an immi-
nent/new event to Civil Protection to monitor, and eventually intervene, in areas with
higher values of lava hazard, without having information on the event's duration and
emission rate that take place.
A further fundamental application category regards the assessment of protective
measures, such as earth barriers or channel digging, for mitigating lava invasion sus-
ceptibility in given areas. To illustrate this kind of application, a northwest-southeast
trending barrier, 2 km long and 20 m high, was considered along the northern margin of
Nicolosi, an urban area with many administrative buildings and tourist facilities for di-
verting lava flows into a valley at the eastern margin of the town without, however, con-
sidering the legal and ethical aspects of such an operation. By querying the simulation
database, all the lava flows that affected the barrier were selected and thus re-simulated
on the modified topography which embeds the presence of the barrier. Similarly to the
case of the applications shown in Figures 4 and 5, an ad hoc susceptibility scenario was
extracted by considering these new simulations (Figure 7a).


Search WWH ::

Custom Search