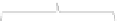Database Reference
In-Depth Information
defined functions (UDF)
. Except for the UDFs, no access via insert, update, or delete
operations is granted on tables of the original sensor image schema, which contains the
image as well as the provenance data. As a result, we prevent the contained data from
unauthorised modification and thus, can ensure integrity and reliability. Obviously, the
performance overhead of this approach is smaller compared to the
modified query en-
gine
approach. Unfortunately, this alternative is not as transparent as the approach above
and a user who gains unauthorised access to the underlying DB can (maliciously) mod-
ify the system behavior, e.g., by altering the UDFs. Currently, we use best practices to
prevent the circumvention of our system. Amongst others, we restricted the adminis-
trative access to FiVe DB to one virtual user. Furthermore, the password for this user
consists of two parts kept by two different person (four eyes principal). Additionally,
we plan to use periodic jobs that check the integrity of the data within FiVe DB when
there is little load on the system.
4.4
Extension of the Watermarking Scheme of Merkel et al.
In our infrastructure, we use the watermarking scheme of Merkel et. al. [22], which is a
combination of compression based techniques and difference expansion (see
Section 2.3). This scheme has two additional features that are advantageous for our
purposes. The first feature is relevant for our fine grained provenance data handling
(general purpose and confidential data). To this end, the watermarking scheme allows
to insert a private message that can be read only with an appropriate key. Moreover,
there can be an optional public part accessible without the key. Second, the scheme
optionally allows to preserve the privacy of the finger print(s) in the image [22].
Watermark message format.
The watermark message is a sequence of n bits:
WM
=
{
0
,
1
}
n
. Furthermore, the message is separated into several blocks that rep-
resent different parts of the message. We show the overall structure of the watermark
message in Figure 7.
Each message starts with a four byte integer showing the length of the
private mes-
sage
block (
l
pr
). Particularly, (
l
pr
+1
) is the first bit of another four byte integer repre-
senting the length of the
public message
block. The encrypted private message consists
of two sub blocks: (1) the Prove Set containing confidential provenance information
and (2) a signature (S) ensuring authenticity and integrity of the image itself
and
of the
confidential provenance information in the Prove Set. Moreover, the message consists
of another block containing the location map (see Section 2.3).
Fig. 7.
Watermark message format