Databases Reference
In-Depth Information
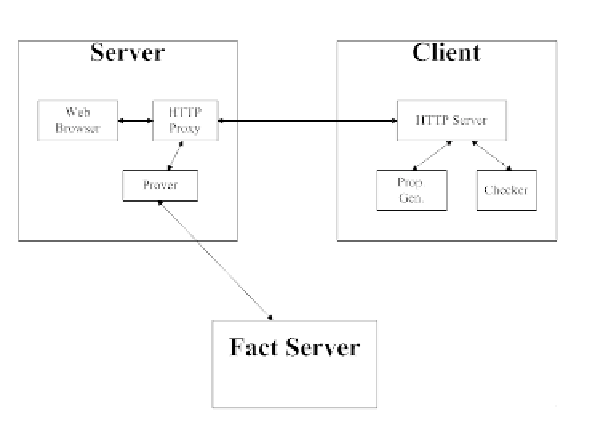
Fig. 3.
The PCA system
request credentials issued by
e
2
asserting the atomic formula
p
(
e
). The body
of a clause having
canReqCred
(
e
1
,e
2
.p
(
e
)) as its head can specify conditions
that must be satisfied before a credential can be disclosed, which is useful in
supporting trust negotiation.
3.6 PCA
PCA (Proof Carrying Authorization) [2, 4] was designed primarily for access
control in web services. Figure 3 shows the components of the PCA system
working in a web browsing environment. HTTP proxies are used to make the
whole process of accessing a web page transparent to the web browser. The
web browser only knows the final result of either a displayed web page that it
attempted to access, or a denial message. The proxy is designed to be portable
and easily integrated into the client system without changing anything inside
the original web browser. As depicted in Figure 3, the client is responsible for
constructing a proof of authorization, which the server need only check for
correctness. This substantially reduces the burden imposed on the server by
the authorization process.
PCA uses higher-order logic to specify policies and credentials, so that
it can be very expressive. Indeed, in general the determination of whether a
proof of authorization exists is undecidable, much less tractable. PCA over-
comes this issue as follows. First, as mentioned earlier, the server only has
to check the proof constructed by the requester, and the checking process is
decidable and tractable. Second, on the client side, the proxy is responsible for
discovering and retrieving credentials, computing proofs, and communicating