Databases Reference
In-Depth Information
S
PPF
-Tree
Authorization Log
argument (t
0
, t
1
)
update
method
find-auth
method
relevant
authorizations
overlays
newly applicable
authorizations
Authorizations
auth_begin
event
removes and
re-overlay
authorizations
auth_end
event
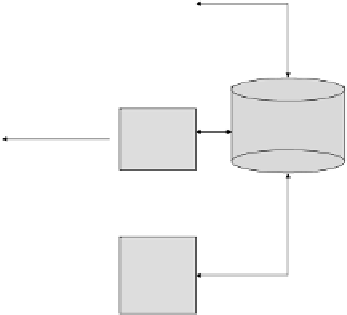
Fig. 2.
Relationship of Authorization Log and S
PPF
-Tree
event, which will overlay the authorization on the tree. On the other hand,
certain overlaid authorizations become invalid when the valid time duration
of the authorization is not applicable to the overlaid nodes. In this case, the
authorization log triggers an auth end event, which will remove the invalid
authorizations from the overlaid nodes and re-overlay on the tree because
the removed ones may satisfy the overlaying conditions of other nodes in the
tree. Also, update must take care of the cases when the time-split occurs.
Time-split creates a new node where some authorizations may be eligible to
be overlaid on it. The authorization log supports a method, called find-auth,
which computes all the authorizations overlapping with the valid interval of
the newly created node. Then, the authorizations as a result of find-auth, will
be overlaid on the new node if it meets the overlaying condition.
User request evaluation is similar to that of
S
TPR-tree except that it can
now evaluate a user request that includes the tracking of moving objects as
well due to the functionality of holding all the updates history. In this case,
only the nodes of which initial creation time and the time when time-split
occurs, if time-splitted (otherwise, this time can be considered as current
time) are overlapped with the time interval of the user request are evaluated.