Databases Reference
In-Depth Information
information and
p
is the customer profile. (3) Similar to the auth-subject hi-
erarchy, in the
Location Hierarchy
the root node represents all members, and
the leaf node represents the members of the most specific representation. (4)
Finally, the
Time Interval Hierarchy
in which an interval is represented by a
node and all its component time intervals are represented as the children of it.
One example would be the case where the root node represents the 24 hours
in a day, and its children nodes could be ”During Working Hours” and ”After
Working Hours.” Observe that in case of the time interval hierarchy, children
nodes are the exact decomposition of its parent node.
Each alphabetical string consists of five substrings that represent the ID,
the object, the subject, the location, and the time. These substrings are drawn
from preprocessed tables where the substrings are unique in each table. The
path from the root to any node in a hierarchy is embedded in the substring
of that node. For instance, the substring 'bcdbf' from the table 1 includes the
letter 'b' for the USA, letter 'c' for Mid-Atlantic, letter 'd' for New Jersey
and the two letters 'bf' for Essex County. Also, all the substrings are made
equal length by adding a padding of letter 'a'. The ASM-trie allows search on
the encoded strings. In the ASM-Trie, the path from the root to a leaf is an
authorization rule.
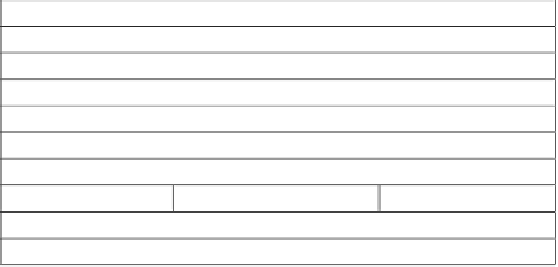
Location
Code without padding Code with padding
All USA
b
baaaa
New England
bb
bbaaa
Mid-Atlantic
bc
bcaaa
...
bc
bcaaa
New Jersey
bcd
bcdaa
New York
bce
bceaa
...
Essex County bcdbe bcdbe
Hudson County bcdbf bcdbf
Table 1.
A Sample from location encoding
Because authorizations are based on this hierarchy, evaluation of a user
request may need to search different places in the hierarchy. Evaluation of
user request is done by first creating a set of search keys. The search process
extracts a letter from the search key and finds its order. This search operation
is recursively performed until the end of the string is reached and an access
control decision is returned if there exists a match.
For example, consider a query submitted by the Hilton for all customers in
Essex County (which is the part of the state of NJ, USA) for a time interval
4:45 to 5:15 PM (which intersects with both time interval leaf nodes ”During
Working Hours” and ”After Working Hours”). Assume that all customers