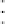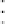Databases Reference
In-Depth Information
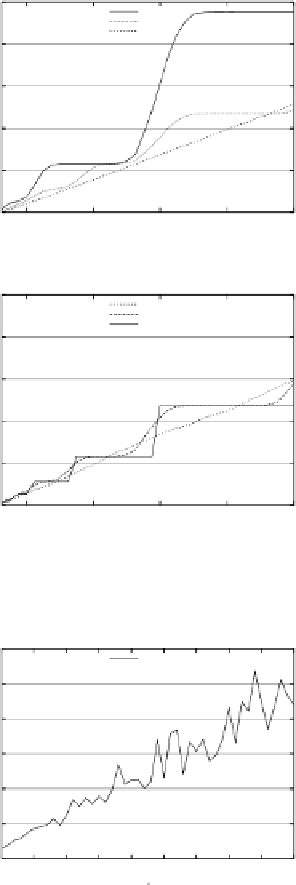
100
intervalCloaking
casper
nnASR
80
60
40
20
0
20
60
100
140
180
k
(a)
C
I
-unsafe algorithms.
100
hilbASR
dichotomicArea
dichotomicPoints
80
60
40
20
0
20
60
100
140
180
k
(b)
C
I
-safe algorithms.
Fig. 8.
Average area with
p
= 100
,
000, uniform distribution of users.
120
dichotomicPoints
100
80
60
40
20
0
10
20
30
40
50
60
70
80
90
100
p (x1000)
Fig. 9.
Computation time of
dichotomicPoints
algorithm with
k
= 80.
6 Conclusion
In this contribution, we identified different privacy threats to users when
location-based services are involved. We then discussed the use of anonymity
for protection, and detailed different techniques for different threats. We also
provided a performance evaluation of the different techniques.