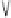Databases Reference
In-Depth Information
Malicious and Legitimate Transactions
Mediator
transaction
type & inputs
Containment
Executor
Uncontainer
DBMS
history
logs
Repair
Manager
database
Damage
Container
alarms
Intrusion Detector
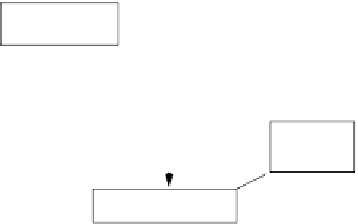
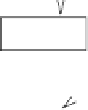
Fig. 5.
Proactive Damage Quarantine
the damage from spreading out during recovery. One problem of the solution
shown in Figure 4 is that its damage quarantine may not be effective, since
it
contains
the damage by disallowing transactions to read the set of data
objects that are identified (by the Damage Assessor) as corrupted. This reac-
tive
one-phase
damage containment approach has a serious drawback, that is,
it cannot prevent the damage caused on the objects that are corrupted but
not yet located from spreading. Assessing the damage caused by a malicious
transaction
B
can take a substantial amount of time, especially when there
are a lot of transactions executed during the detection latency of
B
. During
the
assessment latency
, the damage caused during the detection latency can
spread to many other objects before being contained.
The approach shown in Figure 5 integrates a novel multi-phase damage
containment technique to tackle this problem. In particular, the damage con-
tainment process has one containing phase, which instantly contains the dam-
age that
might
have been caused (or spread) by the intrusion as soon as the
intrusion is detected, and one or more later on uncontaining phases to uncon-
tain the objects that are mistakenly contained during the containing phase,
and the objects that are cleaned. In this approach, the
Damage Container
will
enforce the containing phase (as soon as a malicious transaction is reported)
by sending some containing instructions to the
Containment Executor
.The
Uncontainer
, with the help from the Damage Assessor, will enforce the uncon-
taining phases by sending some uncontaining instructions to the Containment
Executor. The Containment Executor controls the access of the user transac-
tions to the database according to these instructions.
When a malicious transaction
B
is detected, the containing phase must
ensure that the damage caused directly or indirectly by
B
will be contained. In
addition, the containing phase must be quick enough because otherwise either
a lot of damage can leak out during the phase, or substantial availability can